A cryptography walkthrought( not so long, lol)
Encryption is the process of scrambling data so that it cant be read by unauthorised parties. The original data is called plain text, and the encrypted is called ciphertext.
| image by google |
Beating the shit out of Cryptography, is it possible?
Of course, but it depends on the time you have. Most popular cyphers are vulnerable to brute force. However, the brute force required much power and time depending on the encryption. Cypher acquires respectability when mathematicians and cryptographers study them and discover that only brute force can break them.
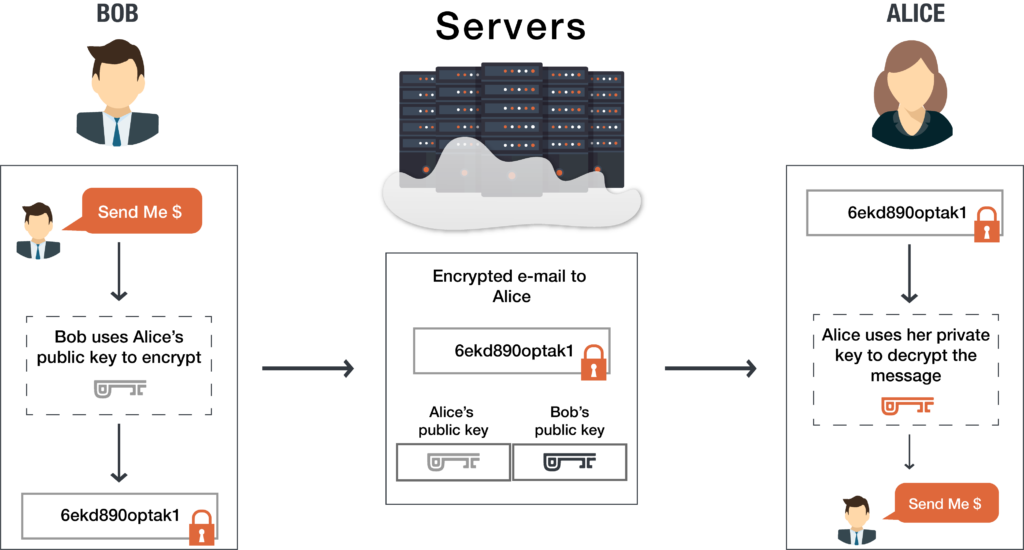
Public and secret key cryptography
Encryption algorithms are known as symmetric and asymmetric.
Symmetric uses the same key to decrypt and encrypt. To ensure dynamic communication over the computer network, asymmetric was introduced.
The public and private keys, related in a mathematically clever way, data are encrypted by one key so that the other key can decrypt it. The public key is distributed so that people can encrypt private data entitled to you and then use your private key to decrypt the data—the public-private key help to solve the key distribution problem.
 |
Hash function: the Hero of the low network bandwidth
The sender can send the original data(unencrypted) to compare when the receiver decrypts the data to ensure data integrity. Yes, we find a genius here, guys. But we just got back to the problem of sending clear data, and it is expensive in time and storage. Therefore, the hash function was used to address this issue.
A hash function is simply a mapping from a large set of data values to a smaller group. When a sender sends a message, the hash value is sent along. The receiver decrypts the message and uses the same hash function to produce the hash value and compare the sender hash value—this helps to know if the data has been altered or not.
However, this simple technique leads to duplicating an equal hash value. Thus, a hash function must be tailored to its intended use.
Another use of the hash function is to detect transmission errors due to hardware failures or software bugs. Signing a large amount of data is expensive in time, as it involves a slow public-key operation. Therefore the hash value is signed and sent along.
A cryptographic hash function must make it computationally infeasible to find two different messages with the same hash or a message with a particular fixed hash. Such a function is collision-resistant (or collision-proof, though that's a bit misleading) and pre-image-resistant. The Cyclic Redundancy Check (CRC) hash commonly used to detect accidental data changes (e.g., an Ethernet frame transmissions) is an example of a noncollision-resistant hash. It is easy to find CRC-32 hash collisions and a well-known attack on SSH-1 is based on this fact.
Examples of cryptographically strong hash functions are MD5 and SHA-1.